某工厂使用一个软件系统变现质检过程的自动化,并逐步替代人工质检。该系统属于( )
外包是一种合同协议。外包合同中的关键核心文件是( )
数据标准化是一种按照预定规程对共享数据实施规范化管理的过程。数据标准化的对象是数据元素和元数据。以下①~⑥中,( )属于数据标准化主要包括的三个阶段。?
①数据元素标准阶段??
②元数据标准阶段??
③业务建模阶段??
④软件安装部署阶段??
⑤数据规范化阶段??
⑥文档规范化阶段?
信息系统的文档是开发人员与用户交流的工具。在系统规划和系统分析阶段用户与系统分析人员交流所使用的文档不包括( )。
( )是构成我国保护计算机软件著作权的两个基本法律文件。
在OSPF路由协议中,路由器在( )进行链路状态广播。
Ping使用了( )类型的ICMP查询报文。
以下关于路由协议的叙述中,错误的是( )。
以下关于RIPv2对于RIPv1改进的说法中,错误的是( )。
以下关于OSFP路由协议的说法中,错误的是( )。
以下关于IS-IS路由协议的说法中,错误的是( )。
以下关于BGP路由协议的说法中,错误的是( )。
在浏览器地址栏输入ftp://ftp.tsinghua.edu.cn/进行访问时,首先执行的操作是( )
在Linux中,用于解析主机域名的文件是( )。
在linux中,可以使用命令( )将文件abe.txt拷贝到目录/home/my/office中,且保留原文件访问权限。
在Linux中,要使用命令“chmod-R xxx/home/abc"修改目录/home/abc的访问权限为可读、可写、可执行,命令中的“xxx”应该是( )。
在Windows中,DNS客户端手工向服务器注册时使用的命令是( )。
Windows Server 2008 R2上内嵌的Web服务器是( )服务器。
Windows中,在命令行输入( )命令可以得到如下的回显。?
Server: UnKnown??
Adress: 159.47.11.80??
xxx.edu.cn??
primary name server = nsl.xxx.edu.cn??
responsible mail addr = mailxxx.edu.cn??
serial = 2020061746??
refresh= 1200(20 mins)?
retry= 7200(2 hours)?
expire = 3600(1 hour)?
default TTL = 3600(1 hour)
以下关于电子邮件服务的说法中,正确的是( )。
用户可以使用( )向DHCP服务器重新请求IP地址配置。
在防火墙域间安全策略中,不是outbound方向数据流的是( )。
以下关于HTTPS的描述中,正确的是( )。
管理员发现交换机的二层转发表空间被占满,清空后短时间内仍然会被沾满,造成这种现象的原因可能是( )。
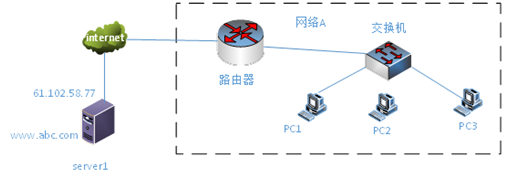
某网络结构如下图所示。PC1的用户在浏览器地址栏中入www.abc.com获取响应页面,而输入61.102.58.77可以正常打开Web页面,则导致该现象的可能是( )。
下面的IP地址中,能够作为主机地址的是( )
下面的IP地址中,不属于同一网络的是( )
PC1的IP地址为192.168.5.16,PC2的IP地址为192.168.5.100,PC1和PC2在同一网段中,其子网掩码可能是( )
下列命令片段含义是( )。
system-view
[HUAWEI] observe-port 1 interface gigabitethernet 0/0/1
[HUAWEI] interface gigabitethernet 0/0/2
[HUAWEI-GigabitEthernet0/0/2] port-mirroring to observe-port 1 inbound
使用( )命令可以显示OSPF接口信息。
GVRP是跨交换机进行VLAN动态注册和删除的协议,关于对GVRP描述不准确的是( )。
与CSMA相比,CSMA/CD( )。
下列通信技术标准中,使用频带相同的是( )。
以下关子WIFI6的说法中,错误的是( )。
以下关于无线漫游的说法中,错误的是( )。
某公司局域网使用DHCP动态获取10.1.0.1/24网段的IP地址,某天公司大量终端获得了192.168.1.0/24网段的地址,可在接入交换机上配置( )功能杜绝该问费再次出现。
项目范围管理过程如下所示,其正确的流程顺序是( )。?
①定义范围??
②核实范围??
③收集需求??
④控制范围??
⑤创建工作分解结构?
某信道带宽为1MHz,采用4幅度8相位调制最大可以组成( ?)种码元。若此信道信号的码元宽度为10微秒,则数据速率为( )kb/s。
某信道带宽为1MHz,采用4幅度8相位调制最大可以组成( )种码元。若此信道信号的码元宽度为10微秒,则数据速率为(? )kb/s。
ARP报文分为ARP Request和ARP Response,其中ARP Request采用( ?)进行传送,ARP Response采用( )进行传送。
ARP报文分别为ARP Request和ARP Response,其中ARP Request采用( )进行传送,ARP Response采用()进行传送。
用户使用ftp://zza.com访问某文件服务,默认通过目标端口为( )的请求报文建立(?) 链接。
某数据中心做存储系统设计,从性价比角度考量,最合适的冗余方式是(?) ,当该RAID配备N块磁盘时,实际可用数为( )块。
某数据中心做存储系统设计,从性价比角度考量,最合适的冗余方式是() ,当该RAID配备N块磁盘时,实际可用数为( ?)块。
某公司中,最大的局域网可容纳200个主机,最小的局域网可容纳20个主机,若使用可变长子网掩码划分子网,其最长的掩码(? )位,最短的掩码()。
某公司中,最大的局域网可容纳200个主机,最小局域网可容纳20个主机,若使用可变长子网掩码划分子网,其最长的掩码( )位,最短的掩码()。
Network security is the protection of the underlying networking infrastructure from (作答此空)access, misuse, or theft, It involves creating a secure infrastructure for devices, users and applications to work in a ( ) manner. Network security combines multiple layers of defenses at the edge and in the network. Each network security layer implements ( ) and controls. Authorized users gain access to network resources. A ( ) is a network security device that monitors incoming and outgoing network traffic and decides whether to allow or block specific traffic based on a defined set of security rules. A virtual ( ) network encrypts the connection from an endpoint to a network, often over the internet. Typically a remote-access VPN uses IPsec or Secure Sockets Layer to authenticate the communication between device and network.
Network security is the protection of the underlying networking infrastructure from ( )access, misuse, or theft, It involves creating a secure infrastructure for devices, users and applications to work in a (作答此空) manner. Network security combines multiple layers of defenses at the edge and in the network. Each network security layer implements ( ) and controls. Authorized users gain access to network resources. A ( ) is a network security device that monitors incoming and outgoing network traffic and decides whether to allow or block specific traffic based on a defined set of security rules. A virtual ( ) network encrypts the connection from an endpoint to a network, often over the internet. Typically a remote-access VPN uses IPsec or Secure Sockets Layer to authenticate the communication between device and network.
Network security is the protection of the underlying networking infrastructure from ( )access, misuse, or theft, It involves creating a secure infrastructure for devices, users and applications to work in a ( ) manner. Network security combines multiple layers of defenses at the edge and in the network. Each network security layer implements (作答此空) and controls. Authorized users gain access to network resources. A ( ) is a network security device that monitors incoming and outgoing network traffic and decides whether to allow or block specific traffic based on a defined set of security rules. A virtual ( ) network encrypts the connection from an endpoint to a network, often over the internet. Typically a remote-access VPN uses IPsec or Secure Sockets Layer to authenticate the communication between device and network.
Network security is the protection of the underlying networking infrastructure from ( )access, misuse, or theft, It involves creating a secure infrastructure for devices, users and applications to work in a ( ) manner. Network security combines multiple layers of defenses at the edge and in the network. Each network security layer implements ( ) and controls. Authorized users gain access to network resources. A (作答此空) is a network security device that monitors incoming and outgoing network traffic and decides whether to allow or block specific traffic based on a defined set of security rules. A virtual ( ) network encrypts the connection from an endpoint to a network, often over the internet. Typically a remote-access VPN uses IPsec or Secure Sockets Layer to authenticate the communication between device and network.
Network security is the protection of the underlying networking infrastructure from ( )access, misuse, or theft, It involves creating a secure infrastructure for devices, users and applications to work in a ( ) manner. Network security combines multiple layers of defenses at the edge and in the network. Each network security layer implements ( ) and controls. Authorized users gain access to network resources. A ( ) is a network security device that monitors incoming and outgoing network traffic and decides whether to allow or block specific traffic based on a defined set of security rules. A virtual (作答此空) network encrypts the connection from an endpoint to a network, often over the internet. Typically a remote-access VPN uses IPsec or Secure Sockets Layer to authenticate the communication between device and network.